Post 38 | The Illusion of Expiry: A Filter, A Code, A Choice
How the Filter Tried to Fool Me
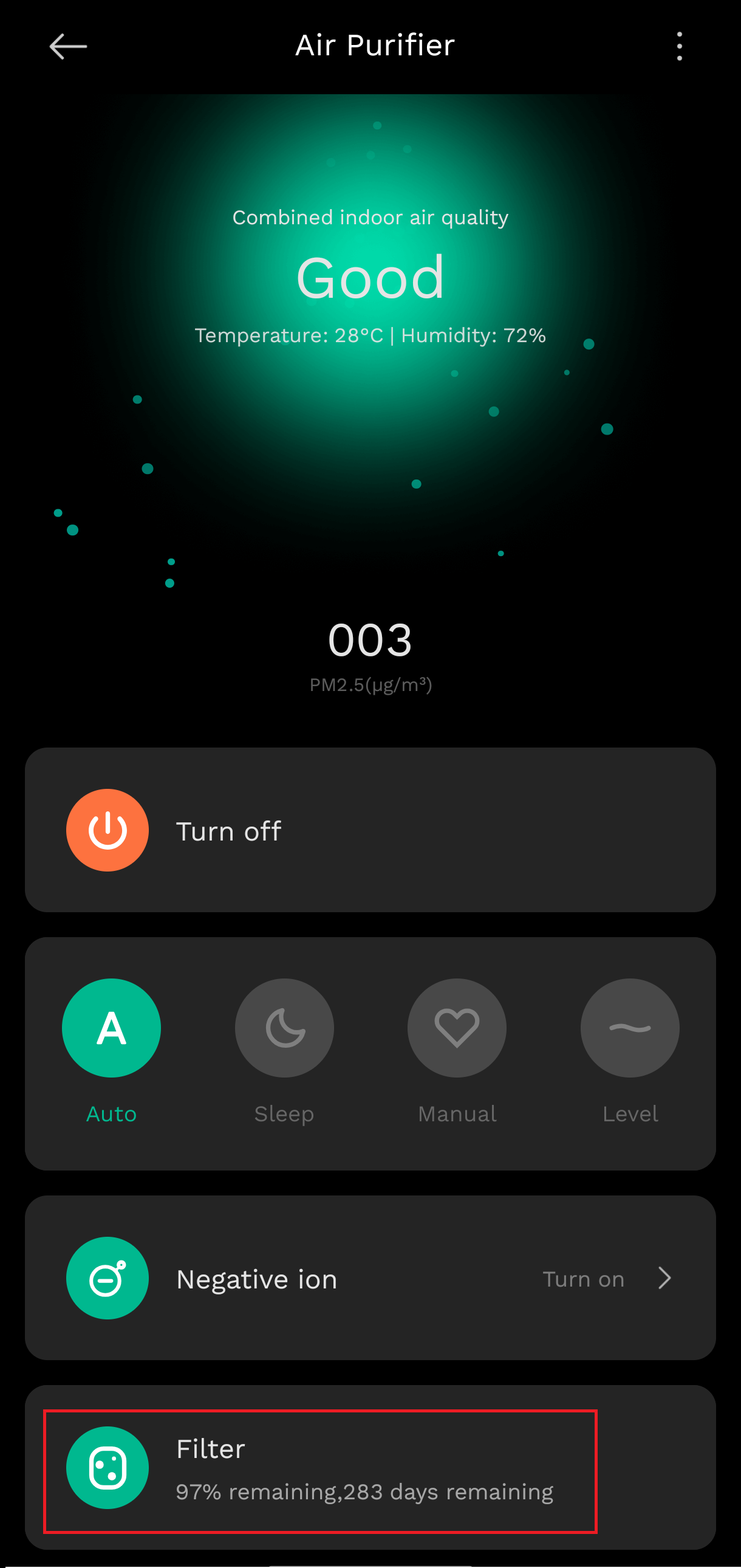
I brought home the Xiaomi 4 Pro air purifier expecting peace. Clean air. Silence. Instead, I got firmware-induced anxiety. Months after careful use and frequent cleaning, the machine lit up my room with a bold proclamation: 0% remaining — replace your filter.
But the air was clean. The filter still functional. And no matter how many times I tried to silence the error, it returned. Not because the filter had failed — but because the system had decided its time was up.
That’s when I realized: this wasn’t about clean air. It was about control.
Expiry by Design: A Filter That Tells Lies
Xiaomi, like many manufacturers, uses an NFC tag embedded in each filter. This tag doesn’t measure dust. It doesn’t assess air quality. It simply tracks time. Once the counter hits zero — regardless of actual performance — the purifier demands you replace the filter. You have no say.
Image 1: Filter expiration notification on the Air Purifier
Unless you learn to talk back.
The Key to the Locked NFC Tag: UID to Password
Every NFC tag has a UID — a unique identifier. Xiaomi’s firmware uses this UID to generate a password using a deterministic method based on the SHA-1 hash.
Let’s walk through an example based on the tag UID: 04A03CAA1E7080, which results in the password CD91AFCC. Lets understand how this password is generated. This Tag ID can be captured using any mobile phone having NFC capabilities which most mobiles do have these days. Just Turn on the NFC on your phone, open the NFC app and your phone too can capture this details.
First, we convert the UID into a byte array:
1
[04, A0, 3C, AA, 1E, 70, 80]
Next, we apply the SHA-1 hash function to this byte array. The resulting hash is:
1
bcaf806333ccf720cd441a167f914fbe6ea4a513
To extract the password, we:
- Convert the first byte of the hash —
BC— to decimal: 188. - Use this number to calculate four indices in the hash:
- 188 % 20 = 8
- (188 + 5) % 20 = 13
- (188 + 13) % 20 = 1
- (188 + 17) % 20 = 5
- Retrieve the corresponding bytes:
- 8th byte:
CD - 13th byte:
91 - 1st byte:
AF - 5th byte:
CC
- 8th byte:
Concatenating these gives us the password:
1
CD91AFCC
Credit to the original reverse engineering effort by Flamingo-tech on GitHub.
This password allows us to authenticate and communicate with the tag.
From Code to Command: Talking to the Tag
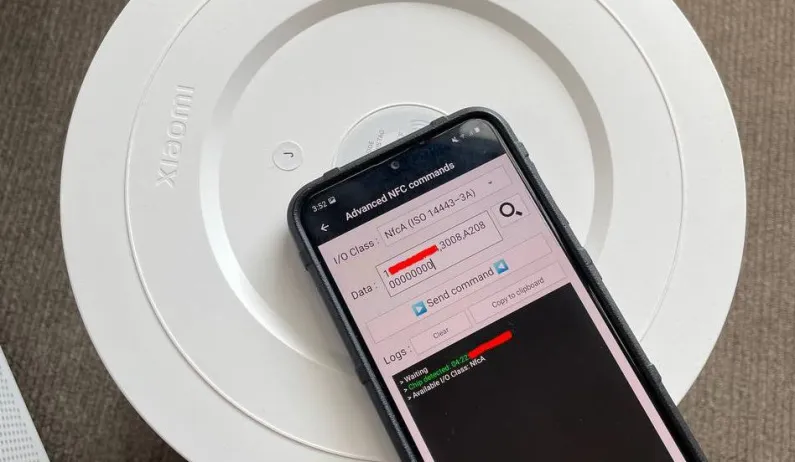
With password in hand, we build a command sequence using standard NTAG213 NFC commands:
1
1B CD91AFCC, 3008, A20800000000
Here’s what each part of the command does in detail:
| APDU Part | Command Type | Meaning and Purpose |
|---|---|---|
1B CD91AFCC | Authenticate | 1B is the PWD_AUTH command; CD91AFCC is the 4-byte password derived from the UID. This command authenticates access to protected memory pages. |
30 08 | Read | 30 is the READ command; 08 refers to block 8 of the NFC memory. This optional step reads the current data of block 8 (useful for verification). |
A2 08 00000000 | Write | A2 is the WRITE command; 08 again targets block 8, and 00000000 is the new value written to that block — effectively resetting the filter usage to 100%. |
These aren’t Xiaomi secrets. They’re part of open NFC standards — they just don’t want you to know it.
Image 2: Using our Mobile Phone, Rewriting the NFC Tag
Anatomy of the Filter Tag
Thanks to prior reverse engineering, we understand the tag’s layout:
| Block | Meaning |
|---|---|
| 4 | Factory ID |
| 5 | Product ID |
| 6 | Timestamp |
| 7 | Serial Number |
| 8 | Usage Counter (this is what we reset) |
Block 8 is the lie. Everything else is metadata. You’re not damaging the filter or the device — just correcting a manufactured fiction.
Reprogramming the Illusion — Step-by-Step
- Install NFC Tools (Android/iOS).
- Scan the tag and confirm UID =
04A03CAA1E7080. - Generate password →
CD91AFCC. - In NFC Tools, go to:
- Other → Advanced NFC Commands
- Set I/O class: NfcA (ISO 14443-3A)
Paste the full command into NFC Tools:
1
1B CD91AFCC, 3008, A20800000000
- Tap your phone to the tag and select ‘send the command’.
- Done. Your filter is now back to 100%.
Image 3: Filter Reset for next 365 Days
But What About the Company’s Right to Profit?
It’s a fair question — one that deserves clarity, not defensiveness.
Most users replace filters annually, often spending ₹3,000–₹4,000.
This forms a recurring revenue model, not unlike printer ink or smart bulbs.
But filters don’t simply “expire.” They degrade based on usage, air quality, and maintenance — not a strict timer.
What’s challenged here isn’t the business — it’s the assumption that the timer knows better than you.
This isn’t bypassing safety. It’s asking: Should control come from inside the machine — or the one breathing beside it?
According to experts:
- HEPA filters can last 12–18 months in clean homes.
- Cleaning them regularly with a vacuum can prolong lifespan.
- Xiaomi’s NFC usage counter is time-based, not performance-based.
So this isn’t cheating. This is regaining the right to decide.
Why It Matters: Health, Money, and Sustainability
- Don’t compromise your health — change the filter when it’s truly dirty.
- But don’t waste a working one just because firmware said so.
- Unnecessary replacements add to e-waste and inflate consumption.
This is not just a hack — it’s a rebalancing.
Acknowledgement
This research was already completed by unethical.info and all credit goes to him. I have replicated his work to:
A. See if it works or not
B. Because I was equally reluctant to change the filter when I knew it still had some life in it.
Image 1 and Image 2 are credited to him.
Also shared via: Hackaday Article